|
|
Note:
I have worked on many UNIX OS and I had to deal with the network: DNS installation
and configuration, NFS configuration, bootp, .... This file contains few personal notes.
This is not a tutorial.
|
Apache is the name of the HTTP server. Apache was originally based on code and ideas found in the most popular HTTP server of the time.. NCSA httpd 1.3 (early 1995). It has since evolved into a far superior system which can rival (and probably surpass) almost any other
UNIX based HTTP server in terms of functionality, efficiency and speed.
Since it began, it has been completely rewritten, and includes many new features. Apache is, as of January 1997, the
most popular WWW server on the Internet, according to the Netcraft Survey.
The ARP protocol (Address Resolution Protocol) is used to obtain the physical address (the ethernet address for example) from the IP address.
| "physical address = ARP(IP address)"
|
Notes:
- The ARP layer is found between the IP and the "physical" layers. Many operating systems provide a hook
to access the ARP table.
- The ARP table is dynamically updated. Hosts on a networks exchange periodically (or when needed) ARP messages in order
to keep the ARP table up to date.
- Many UNIX systems provide command to manipulate the ARP table. Under AIX 3.2 you can use the "arp" command to
add (or delete) an entry in the ARP table for example.
On common usage the baud rate of a modem is how many bits it can send
or receive per second. Technically, baud is the number of times per
second that the carrier signal shifts value - for example a 1200
bit-per-second modem actually runs at 300 baud, but it moves 4 bits per
baud (4 x 300 = 1200 bits per second).
If you have diskless machine (for example) on your network, you probably need a way to boot over the network. To do that you should use "BOOTP" or "DCHP" (DHCP is an evolution of BOOTP).
Bootp is an alternative to RARP that allows the machine to obtain an IP
address, gateway address and netmask using UDP and IP can be used over dialup SLIP/PPP connection.
The follwing information shows how to configure the last bootpd version.
Compatibility
This file contains the source code for bootpd 4.3. You can compile it under the
following UNIX systems:
- Linux 1.1.80+
- IBM AIX 4.2 (and probably other version of AIX)
- DEC/OSF1 on the Alpha
- Control Data EP/IX 1.4.3 system, BSD 4.3 mode
- Control Data EP/IX 2.1.1 system, SVR4 mode
- IRIX 5.X (Silicon Graphics
- SCO (pah!) SYSV rel 3.2
- SunOS 4.X
- Solaris 2.X (i.e. SunOS 5.X)
- Solaris 2.X with GCC (i.e. SunOS 5.X with GCC)
- UNIX System V Rel. 3
- UNIX System V Rel. 4
- AT&T/GIS - Both AT&T StarServer and NCR 3000. May work for others using Wollongong's WIN-TCP
- and probably other systems
We have tested this version of bootpd under AIX 4.2 and Linux - it
works good.
Installation notes
To install bootpd 4.3:
- Unzip and untar tye file bootpd-4.3.tar.gz
- Edit the file "Makefile" to see what target are supported.
- Read the file "Installation". This file describes how to:
- Build bootpd
- Install bootpd
- Configure your system
Configuration notes
Configuration files
| /etc/services
|
Assign the following resources to the network services:
- A port number
- A protocol (UDP or TCP)
|
| /etc/inetd.conf
|
Whenever a request for service arrives, the inetd daemon is tricked into running the tcpd program instead of the desired server. tcpd logs the request and does some additional checks. When all is well, tcpd runs the appropriate server program and goes away.
So in order to allow bootp to be executed whenever a bootp request arrived, you need to tell the bootp daemon what to do when a bootp request arrives. |
| /etc/bootptab
|
Specific bootp configuration.
|
Sample configuration files
This is only an example. Your system may need a specific configuration.
| /etc/services |
bootps 67/udp
bootpc 68/udp
tftp 69/udp |
| /etc/inetd.conf |
bootps dgram udp wait root /usr/sbin/bootpd bootpd -i
tftp dgram udp wait root /usr/sbin/in.tftpd in.tftpd
|
| /etc/bootptab |
bench:bf=/tmp/vx1.st:ht=ether:ha=0x0000de46142a:ip=92.40.56.7:sm=255.255.255.192
- "Bench" is the name of the target.
- "/tmp/vx1.st" is the file the target wants to download.
- "ether" means that the target address is an Ethernet address.
- "0x0000de46142a" is the Ethernet address of the target.
- "92.40.56.7" is the IP address of the target.
- "255.255.255.192" is the subnet mask
Notes:
- Do not forget the "0x" at the beginning of the Ethernet address.
- The Ethernet address must have exactly 12 characters (+ the 2 characters "0x"). "0xde46142a" is not the same that "0x0000de46142a".
the board.
|
There are 4 types of broadcast:
- The limited broadcast.
- The Net-directed broadcast.
- The Subnet-directed broadcast.
- The All subnet-directed broadcast.
Please refer to the Network mask section for notations.
Limited broadcast
The limited broadcast address is "255.255.255.255". A message that uses this address
(as a destination address of course) is nerver forwarded by a router. Note that this
address can be used as a destination address ONLY.
|
Net-directed
The Net-directed broadcast address is associated with the class of the network.
To obtain the Net-directed broadcast address of a specific network, put all the bits of the "HOST portion"
("SUBnet portion" if defined + "host portion") to 1. The rest (the "network portion") remains intact.
example:
- class A network: "x.255.255.255" ("x" = "network portiion").
- class B network: "x.y.255.255" ("x.y" = "network portiion").
- class C network: "x.y.z.255" ("x.y.z" = "network portiion").
By default, a Net-directed broadcast must be forwarded by routers.
|
Subnet-directed
The Subnet-directed broadcast address is associated with the subnet portion
(in green in the following examples) of the netmask. It denotes
all the hosts on a specific subnetwork. To obtain the Subnet-directed broadcast address
put all the bits of the "host portion" to 1 (the rest: "SUBnet portion" + "network portion" remains
intact).
Example 1:
Class B network (128.1.0.0) with netmask "128.1.255.0".
Note that this netmask allows you to create up to (2^8-2) = 254 sub-networks.
In "binary" the netmask is "128.1.11111111.00000000".
- The Subnet-directed broadcast address for the subnet "128.1.00000001.00000000" (128.1.1.0) is "128.1.00000001.11111111" (128.1.1.255).
- The Subnet-directed broadcast address for the subnet "128.1.00000011.00000000" (128.1.3.0) is "128.1.00000011.11111111" (128.1.3.255).
- ...
Example 2:
Class B network (128.1.0.0) with netmask "128.1.192.0"
(wich allow you to create up to 2 sub-networks).
In "binary" the netmask is "128.1.11000000.00000000".
- The Subnet-directed broadcast address for the subnetwork "128.1.10000000.00000000" is "128.1.10111111.11111111" (192.1.191.255).
- The Subnet-directed broadcast address for the subnetwork "128.1.01000000.00000000" is "128.1.01111111.11111111" (192.1.127.255).
|
All-Subnet directed
To obtain the All-Subnet directed broadcast address of a specific network, put all the bits of the "HOST portion" ("SUBnet portion" + "host portion") to 1. The rest (the "network portion") remains intact.
Note:
It is easy to be confused between a All-Subnet directed broadcast address
and a Net-directed broadcast address. These 2 addresses are identical.
Let's take an example: The destination address "128.1.255.255" is a
All-Subnet directed broadcast address if the destination network "128.1.0.0" is
subneted. Otherwise, if the destination network is not subneted, it is a Net-directed broadcast address.
|
A set of rules that describe how a Web Server communicates with
another piece of software on the same machine, and how the other piece
of software (the CGI program) talks to the web server. Any piece of
software can be a CGI program if it handles input and output according to
the CGI standard. Usually a CGI program is a small program that takes
data from a web server and does something with it, like putting the
content of a form into an e-mail message, or turning the data into a
database query. You can often see that a CGI program is being used by
seeing "cgi-bin" in a URL, but not always.
A domain name is just an index in the DNS database.
Example: "linux.org" is a domain name.
domain
The notion of domain is related to the organisation of the domain names. Practically, a domain name is a group of word, separated by dots (ex: "My_Computer.linux.org"). This notation shows the organisation of domains. Let's take an example:
Considering the following domain name: "ar.ld,cpp.gcc.gnu.org.".
| ar.ld,cpp.gcc.gnu.org.
| "ar.ld,cpp.gcc.gnu" is part of the "org." domain. |
| ar.ld,cpp.gcc.gnu.org.
| "ar.ld.cpp.gcc" is part of the "gnu.org." domain. |
| ar.ld,cpp.gcc.gnu.org.
| "ar.ld.cpp" is part of the "gcc.gnu.org." domain. |
| ...
| ...
|
Notes:
- that a domain is only a logical notion related to the DNS database. You may think that a domain is related to a geographical area: that's could be the case, but not necessarily. For example 3 computers in 3 different continents can be part of a domain.
- A domain is not Necessarily associated with a network mask. It could be the case, but it is not an obligation.
- The domain name "toto.titi.gnu.org." means that "toto.titi.gnu" is part of the "org." domain (as "ar.ld,cpp.gcc.gnu" in the previous example).
zone
The definition of a zone is not as simple as the definition of a domain. A zone is a "part of the network" that is administrated by a name server. A name server doesn't administrate a domain, it administrates a zone. We "could" say that a domain is made of zones, but it is not absolutly correct. More precisely a domain is administrated by zones.
The Domain Name Server administrates the Domaine name Service. The Domaine name Service is a distributed database that contains informations about the domain name. This distributed database is locally administrated by "softwares" called name servers.
There are many implementations of DNS, but the most popular is BIND. BIND has many avantages:
- BIND can be used on almost all UNIX systems and on Windows NT.
- BIND is developped by an excellent programmer team. It's a good software (robust, performant, ...).
- BIND is the most used on the internet.
- BIND is free !
Click here to see how to configure BIND.
Ethernet II address:
MAC (or NIC) address
|<--------------------------------->|
| | |
| Vendor ID | Serial number |
|<--------------->|<--------------->|
_____ _____ _____ _____ _____ _____
| | | | | | |
|_____|_____|_____|_____|_____|_____|
| |
| |
Most significant Least significant
byte byte
- The least significant bit of the most significant byte is called the "multicast
bit" (1 if the address is a multicast address, 0 otherwise).
- The Vendor ID is only defined for a unicast address.
|
| Unicast address
|
Most significant byte: even value (0x00, 0x02, ...) <=> Multicast bit set to 0.
|
| Multicast address
|
Most significant byte: odd value (0x01, 0x03, ...) <=> Multicast bit set to 1.
ALWAYS a destination address (never a source address).
|
| Broadcast address
|
FF:FF:FF:FF:FF:FF
ALWAYS a destination address (never a source address).
|
How to distinguish a "Ethernet II header" from a "IEEE 802.3 header" ?
Eternet II
- destination address: 6 bytes.
- sender address: 6 bytes.
- protocol type: 2 bytes.
- ...
|
IEEE 802.3
- destination address: 6 bytes.
- sender address: 6 bytes.
- protocol type: data length.
- ...
|
- The "data length" of the "IEEE 802.3" is a number between 0x0000 (included) and 0x05dc (included) => the maximum
size of the protocol data is 1500 (= 0x05dc) bytes. The minimun size for a packet (header+data+CRC) is 64 bytes.
- The "protocol type" of the "Ethernet II header" is a number greater than 0x05dc. See RFC 1700 for the list of
assigned protocol types.
The finger command appeared in 3.0BSD. It allows you to get informations about a user.
Practically a Fully Qualified Domain Name is a domain name that ends with a ".". For example "marvin.linux.org." (note the "." at the end) is a FQDN.
This notation is related to DNS theory. In DNS, domain names are arganised like the UNIX file system. The ".' at the end of the domain name is equivalent to the "/" at the beginning of a UNIX file path.
Example:
| UNIX directory
| Domain name |
"/bin/progs/my_prog"
- "bin" is a subdirectory of the root directory "/".
- "progs" is a subdirrctory of the directory "bin".
- "my_prog" refers to a particular program of the "/bin/progs" directory.
| "marvin.linux.org"
- "org" is a subdomain of the root domain ".".
- "linux" is a subdomain of the domain "org".
- "marvin" refers to a particular computer of the "limux.org." domain.
|
The ftp command appeared in 4.2BSD. The File Transfer Protocal is used to download (or upload) files.
The protocol for moving hypertext files across the Internet. Requires an
HTTP client program on one end, and an HTTP server program on the
other end. HTTP is the most important protocol used in the World Wide
Web (WWW).
The ifconfig command is used to configure the network interface (for example the ethernet card, the token ring card, the PPP link, ...). Basically the ifconfig command assigns an IP address to the interface.
| Example
| ifconfig eth0 192.70.56.1 netmask 255.255.255.0 up
In this example we assign the IP address 192.70.56.1 to the first ethernet card (eth0) of you "computer". The up argument means "activate this interface".
|
Fragmentation occurs when the IP layer wants to send a datagram longer that the link layer
MUT (Maximum Transmission Unit).
Example:
The Ethernet MTU is 1500. This means that the size of the longest ethernet datagram is
1500 bytes long.
------------------------------------------------------------------------------------
| | | |
| Ethernet header | IP header | application data |
| | | |
------------------------------------------------------------------------------------
| | |
|<--------------->|<-------------------------------------------------------------->|
14 bytes sizeof(Ethernet datagram) <= MTU (1500 bytes)
The application layer needs to send a 5000 bytes long datagram. The IP layer consults
the link layer to know the MTU associated with the network interface. Assuming that the
application uses the ethernet interface, the MTU is 1500. Therefore the IP layer needs to
frament the big datagram into smaller pieces.
The sender will send to the receiver many "small" datagrams. In order, for the receiver, to
reassemble these datagrams, the sender must include information: this is done by the IP layer.
The IP header contains information that allow the receiver to reassemble the original (big)
datagram.
| IP header |
/* structure of an ip header */
struct S_ip
{
#ifdef LITTLE_ENDIAN_BITFIELD
unsigned short ip_length:4;
unsigned short ip_version:4;
#else
unsigned short ip_version:4;
unsigned short ip_length:4;
#endif
unsigned char ip_tos;
unsigned short ip_total_length;
unsigned short ip_id;
unsigned short ip_flags;
unsigned char ip_ttl;
unsigned char ip_protocol;
unsigned short ip_cksum;
unsigned int ip_source;
unsigned int ip_dest;
};
|
The ip_flag field of the IP header is 16 bits long and has the following organization:
- 1 bit: reserved.
- 1 bit:
- 0 means "this datagram can be fragmented".
- 1 means "this datagram can NOT be fragmented".
- 1 bit:
- 0 means that this datagram is the final fragment or the only fragment.
- 1 means that there is more fragments to follow.
- 13 bits: indicates the fragment offset (per 64 bits) from the start of the original
datagram.
Notes:
Setting the second bit to 1 is dangerous unless you know exactly the route follwed by
the datagram. If only one section of this route has a MTU inferior than the size of
your datagram, the datagram will be lost. The router (or gateway) won't be able to
fragment the datagram so the datagam will be discarded.
Kermit software offers a consistent approach to file transfer, terminal emulation, script programming, and character-set conversion on hundreds of different hardware and operating-system platforms, using diverse communication methods. Kermit can be use instead of "cu" or "tip".
Kermit can be find at: http://www.columbia.edu/kermit/
A multicast address indicates a group of hosts with something in common (note that this
this is not a broadcast address).
A name server is a program that store informations about the domain name space. A name server keeps informations about his own zone. Informations about a zone are called zone data files or just data files.
There are two kinds of name servers:
- primary master name: the primary master name server reads informations about its zone directly from its host.
- secondary master name: a secondary master name server reads informations about its zone form a primary master name server (or from another secondary master name server). This kind of name servers can be seen as a relays. Periodically they check the validity of their own zone data files and reloat them if necessary.
Both primary and secondary name servers are authoritative for their zone. secondary master name server are useful because you only have to maintain one primary master name server - the others mane servers of your zone will automatically adjust their zone data files.
The net-tools is a collection of basic network utilities used under Linux. In this collection you can find:
- the route command
- the ifconfig command
- the telnet deamon (telnetd)
- the TCP deamon (tcpd)
- ...
| Notes:
|
- If you want to install the net-tools (wich is pretty easy), read carefully the installation notes. It is important that you choose the correct version according to you kernel version.
- The net-tools can be found at ftp://ftp.uk.linux.org/pub/linux/Networking/base/.
|
| Class
| from
| to |
| A
| 1.0.0.0
| 127.0.0.0 |
| B
| 128.0.0.0
| 191.255.0.0 |
| C
| 192.0.0.0
| 223.255.255.0
|
| Red:
| Network portion |
| Green:
| HOST portion
|
Network portion, SUBnet portion and host portion
An IP address is composed of:
- the "network portion".
- the "HOST portion".
IP address = [Network portion][HOST portion]
| |
|<--------------------------->|
32 bits
The size of the "network portion" depends on the class of the address:
- class A: 1 byte.
- class B: 2 bytes.
- class C: 3 bytes.
The "HOST portion" (HOST in uppercase) can also be divided into:
- the "SUBnetwork portion" (or "SUBnet portion"). 2 bits minimum. The "SUBnet portion" can NOT be all 0 or all 1.
- the "host portion" (host in lowercase). The "host portion" can NOT be all 0 or all 1.
IP address = [Network portion][SUBnet portion][host portion]
| | | |
| |<------------>| |
| > 2 bits |
| |
|<------------------------------------------->|
32 bits
The subnet portion is used to divide a network in subnetworks. Let's take the class C network "u.x.y.z". We can take bits from the HOST portion "z" to create subnetworks.
| "SUBnet and host portion" (byte "z")
| decimal value
| number of subnetworks
| number of hosts per subnetwork |
| 1100 0000
| 192
| 2
| 62 |
| 1110 0000
| 224
| 6
| 30 |
| 1111 0000
| 240
| 14
| 14 |
| 1111 1000
| 248
| 30
| 6 |
| 1111 1100
| 252
| 62
| 2
|
Note that:
"number of subnetworks" = 2^S - 2 where S = Size of the "SUBnet portion" in bits.
The "-2" comes from the fact that you can't have a "SUBnet portion" of all 0 or all 1.
|
"number of hosts per subnetwork" = 2^H - 2 where H = Size of the "host portion" in bits.
The "-2" comes from the fact that you can't have a "host portion" of all 0 or all 1.
|
Netmask: definition
To obtain the netmask:
- Put all bits of the "network portion" to 1.
- Put all bits of the "SUBnet portion" to 1.
- Put all bits of the "host portion" to 0.
Example
Considering the class B nerwork 128.70.0.0. The addrese of a hote on this network is 128.70.x.y (with x and y between 0 and 255). To create 2 subnetworks we use the following network mask:
255.255.192.0, or in binary 11111111.11111111.11111111.11000000.00000000
| Red:
| network portion |
| Blue:
| SUBnet portion |
| Green:
| Host portion
|
The 2 subnetworks are (remember that the "SUBnet portion can NOT be all 0 or all 1!):
| Network N1
| 01000000.00000000 |
| Network N2
| 10000000.00000000
|
Remark 1: Why a "Subnet portion" of 1 bit length is fobidden ?
Imagine that you have the following network mask for a class B network:
255.255.128.0 <=> "255.255".10000000.00000000
Then the subnetworks should be:
- "255.255".10000000.00000000 ("SUBnet portion": all bits to 1).
- "255.255".00000000.00000000 ("SUBnet portion": all bits to 0)
This is imposible because the "SUBnet portion" can NOT be all 0 or all 1.
Remark 2: Why you can not have the netmask "192.70.56.254" ?
"192.70.56.x" is a class C IP address. The netmask "192.70.56.254" is in binary:
"192.70.56".11111110
You have 1 bit for the host portion. Therefore, for the subnet "xxxxxxx", you can have the hosts:
- "192.70.56".xxxxxxx0
- "192.70.56".xxxxxxx1
This is impossible because the "host portion" can NOT be all 0 or all 1.
NFS means Network File System and it is used to share files over a network. The implementation of NFS depends on the OS you use, but they are compatible. It means that you can share files between a Linux host and a Solaris host (even if the Solaris implementation of NFS is very particular !).
NFS basics
Basically, you share files between 2 hosts. But physically the files you share are on one of the 2 hosts - this host runs the NFS server. The other host runs the NFS client.
On the NFS server you have to say something like: "I allow this client to access these files". When you do that, you "export" the files you want to share. Usually you use a file called /etc/export to specify the following informations:
- the directory(ies) you want to share.
- the hosts allowed to access these directories.
- the permission (ex: read/write) you give them.
On the NFS client you "make a link between your file system and the server file system". To do that you use the mount command. Usually the syntax is:
mount NFS_Server_Host_Name:Directory_Name_On_The_Server Directory_Name_On_The_Client
| NFS Client
| NFS Server |
This host has a directory /mnt. And, from this host you want to access
the /dir directory on the NFS Server.
mount NFS_Server:/dir /mnt
| This host has a /dir directory and it allows the NFS Client to acess
this directory. The /etc/export file should contain (for Linux at
least) something like:
Local_Dir_Name Client_Name(rw)
This means that the server allows the host Client_Name to mount the
directory (on the server of course) Local_Dir_Name in Read/Write mode.
|
Note: In the /etc/exports file you can specify MANY options. Under Linux
type "man exports" to see all the options.
The `loopback' interface is a special type of interface that allows you to make connections to yourself. The IP address of this interface is 127.0.0.1.
Modem (MOdulator, DEModulator)
A device that you connect to your computer and to a phone line, that
allows the computer to talk to other computers through the phone
system. Basically, modems do for computers what a telephone does for
humans.
The nslookup command is used to query name servers. nslookup emulates a resolver and/or a name server behaviors.
A packet is a chunk of information sent over a network. Each packet contains the
destination address, the senders address, error control information, and
data.
PPP (Point to Point Protocol) is a protocol for sending internet traffic over telephone lines. It is better than SLIP.
A socket is related to a process (application). Basically a socket is the association of:
- An interface (<=> an IP address).
- A port number.
- A protocol: UDP or TCP (note that there is some special kind of sockets that are not
associated with a specific protocol).
To open a socket:
- You create a socket ID with the function socket().
- You attach the socket to an interface using the function bind().
Note: Special sockets are "SOCK_RAW" and "SOCK_PACKET" (Linux specific) sockets.
The RARP protocol (Reverse Address Resolution Protocol) is used to obtain the IP address from the physical address (the ethernet address for example).
| "IP address = RARP(physical address)"
|
note: RARP is used with bootp.
If an application (Netscape for example) needs to know the IP address associated with a given WEB address (like "font.edit.sa.com" for example), it asks its local name server (via the resolver). If the local name server can't find the answer, it asks other name sever. This can be done by two different ways:
- An iterative query: May be the queried name server doesn't know the answer, but he knows a name server that may know it. So your local name server won't receive the IP address Netscape requested, but it will receive the IP address of another name server. And so on until it contacts a name server who knows the answer (or who is sure that there is no answer).
- A recursive query: The queried server will do "all the job" for you. It will give you the answer.
A resolver is the interface between the programs (who need to convert names into IP address) and the name server.
Note: the resolver can be a program but not necessarily. In BIND for example, the resolver is just a set of librairy.
Routing information protocol: used to find the best path between 2 hosts. RIP uses ICMP (Internet Control Message Protocol). ICMP can detect if a path is not a good choice.
The rlogin command appeared in 4.2BSD. Rlogin starts a terminal session on a remote host.
There are 13 root name sevrers in the world. These special name servers administrate the root zone. A root name sevrers only knows about its own zone (like evry name servers), but it knows which name server to ask for.
| Example:
| You want to know the IP address of "font.edit.sa.com".
Your application (ex: Netscape) makes a request to your local name server (via the resolver). If your local name server knows the answser then you are all set. If it doesn't know the answer, then your local name server
will make a request to one of the root name servers.
The root name server doesn't know the IP address of "font.edit.sa.com". But it knows the IP address of the name server of the "com" zone. So it will send a message to your local name server telling something like:
"I don't know the answer, but ask the name sever of the com zone - I give you his IP address, it may know".
The name server of the "com" zone doesn't know the answer but it will give you the address of another name server ... and so on. At the end you will receive the IP address of a name server who knows the answer.
This process is called resolution.
|
Under UNIX the route command is used to add a "path" to:
- a single host
- a network (with many hosts)
Basically you say: "to send a message to this host you've got to use this gateway. If you need to send a message to an host on a different network than your local network(s), you've got to use a gateway. The route command tells the kernel (at least under Linux) what gateway to use.
| Example
|
Under Linux to specify a new route to a network you can use:
route add -net Network netmask NetMask gw GatewayName
- Network can be an IP address (ex: 92.0.0.0) or a name (ex: LinuxNetwork). You can use names instead of IP address if you have edited the /etc/networks file.
- NetMask is a network mask (ex: 255.255.255.0).
- GatewayName can be an IP address (ex: 192.70.56.1) or a name (ex: marvin). You can use names instead of IP address if you have edited the /etc/hosts file.
Remarks:
- In this example the gateway is added to the default interface (for example eth0). You can specify the interface. The route command has many other options, see the man page.
- On other UNIX OS the syntax may be different, but it is very similar (there aren't mant way to say: "I want to add this gateway" !).
|
The routet table is used by IP to determine which interface it should send
a datagram. The route contains the folowing informations:
For each network are associated:
- An interface
- A "gateway" between at least 2 networks
ex: This this the route table of the host My_Host on the network My_Network.
| Network
| gateway
| interface |
| My-Network
| -
| eth0 |
| N1
| -
| eth1 |
| N2
| Bridge_1
| eth0 |
| All_Unknown_Network
| Bridge_2
| eth0
|
My_Host has 2 interfaces: eth0 and eth1 (eth for ethernet). According to the route table:
- eth0 is connected to the network My_Network.
- eth1 is connected to the network N1.
My_Host is directly connected to My_Network and N1, so no gateway is needed to send message to My_Network or N1.
To send a message to the network N2, My_Host must use the gateway Bridge_1.
And for all unknown network (not My_Network, N1 or N2) then the default gateway is Bridge_2.
The rsh command appeared in 4.2BSD. Execute command on a distant host.
A Self healing network has no hard coded path between the source and the destination
hosts. A datagram can take any path to go from one host to another, there is no central
control. A single failure or a group of failure between hosts won't break the
connection between hosts. an IP networks are examples of Self healing networks.
SLIP is a protocol for sending internet traffic over telephone lines. You can can use it to conect you Linux station to the internet. But it is recommended to use PPP instaed of SLIP.
The main protocol used to send electronic mail on the Internet. SMTP
consists of a set of rules for how a program sending mail and a program
receiving mail should interact. Almost all Internet email is sent and
received by clients and servers using SMTP, thus if one wanted to set up
an email server on the Internet one would look for email server software
that supports SMTP.
The RFC 821 that describes the SMTP protocol specify that: "The SMTP design is based on the
following model of communication: as the result of a user mail request, the sender-SMTP
establishes a two-way transmission channel to a receiver-SMTP". In other words the sender
and the receiver open a TCP connexion. This explains why your IP address is always recorded
by the receiver. Of course you can use a chain of remailers, but the IP address of the last
remailer will be recorded by the receiver. If the remailer does not delete all information about
the incoming mails, you can track the message back (if you can physically access the remailer).
A protocol designed by Netscape Communications to enable encrypted,
authenticated communications across the Internet. SSL used mostly (but
not exclusively) in communications between web browsers and web
servers. URLšs that begin with "https" indicate that an SSL connection
will be used.
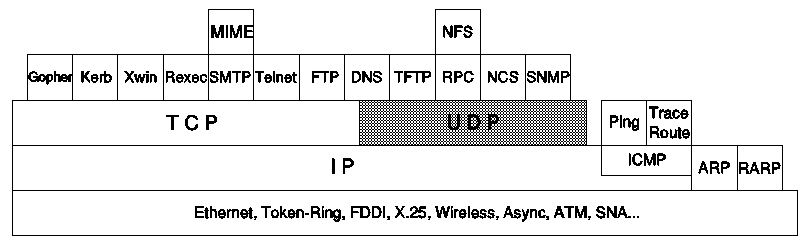
| TCP / IP Architecture |
|
UDP is basically an application interface to IP. It adds no reliability, flow-control or error recovery to IP. It simply serves as a "multiplexer/demultiplexer" for sending and receiving datagrams, using ports to direct the datagrams. UDP provides a mechanism for one application to send a datagram to another.
TCP provides considerably more facilities for applications than UDP, notably error recovery, flow control and reliability. TCP is a connection-oriented protocol unlike UDP which is connectionless. Most of the user application protocols, such as TELNET and FTP, use TCP.
Under Linux tcpd is very important: access control facility for internet services.
The tcpd program can be set up to monitor incoming requests for:
- telnet
- finger
- ftp
- exec
- rsh
- rlogin
- tftp
- talk
- comsat
- and other services that have a one to one mapping onto executable files.
How tcpd proceed ? whenever a request for service
arrives, the inetd daemon is tricked into running the tcpd
program instead of the desired server. tcpd logs the
request and does some additional checks. When all is well,
tcpd runs the appropriate server program and goes away.
The Telnet command appeared in 4.2BSD. It allows you to login to a distant system.
The telnet command is used to communicate with another host using the
TELNET protocol.
The tftp command appeared in 4.3BSD (Trivial File Transfer Protocol). Mainly to boot using bootp.
To reduce the number of queries, name servers use the "caching" process. When a name server receives an answer, it will keep it in case somebody asks it the same question. But it should not keep it forever because this information may become wrong in the future (the host disappears for example). The administrator of the name server has to set a TTL (Time To Live) value. The TTL value specifies the period of time the information will stay in the cache.
- a small value fot the TTL ensures that you keep up to date informations in your cache. But it increases the number of queries for the name server.
- a big value for the TTL reduces the number of queries to the name server. But the name server cache may contain out of date informations.
Unicast address: this address indocates a specific host on the network (the opposite, the broadcast address
indicates all the hosts on the network).
The standard way to give the address of any resource on the Internet that
is part of the World Wide Web (WWW).
This file is used to configure the RARP daemon. The format of the "/etc/ethers" file is very simple:
| ethernet address
| host name
|
notes:
- The "host name" should be declared in the "/etc/hosts" file.
- The format of the ethernet address is: xx:xx:xx:xx:xx:xx
This file is used to configure the NFS server.
This very simple file contains only one line: the Fully Qualified Domain Name (without the trailing dot) of your host. This file is read at the boot precess.
The /etc/hosts file provides a simple database of "computer" names against network addresses. The format is very simple:
ComputerName IP_Adress
| Example
| |
| power
| 192.56.70.1 |
| marvin
| 192.48.40.2
|
This file is used for resolving hostnames. The resolving process is done by the resolver. The following array shows the list of parameters for
/etc/resolv.conf.
| parameter
| value
| explaination |
| order
| bind and/or hosts
| Order in which services for resolving for a host name are called.
the bind value means: "use the name server
(BIND)".
the hosts value means: "use the /etc/hosts
file". |
| multi
| on or off
| Determines if a machine in /etc/hosts is allowed
to have multiple IP address. |
| nospoof
| on
| Just influences spoofing of the nameserver without any other consequences. |
| alert
| on or off
| Just influences spoofing of the nameserver without any other consequences. |
| trim
| "Domain_Name"
| This parameter is useful. When you enter a hostname without any domain name
(ex: MyComputer instead of MyComputer.MyDomainName) the
string "Domain_Name" is added at the end of the hostname.
|
If you use BIND 8 The /etc/named.conf file is read by the named daemon when it starts up. This file tells named wich configuration files it must use. If you use BIND 4.x, then named expects the file /etc/named.boot as a starting file.
| note:
| You can specify another starting file by using the "-b" option. For example
you can type:
named -b StartingFileName
you can force named to reload its configuration files at any time. To do
that you send to named the HUP signal:
kill -HUP Named_Process_Id
|
The /etc/networks file provides a simple database of network names against network addresses. The format is very simple:
NetWorksName NetworkMask
| Example
| |
| math
| 92.0.0.0 |
| polynet
| 192.25.0.0
|
/etc/protocols contains the protocol numbers of the protocols that use the IP layer.
This file is related to BIND. Basically this file tells the resolver what to do when you ask for an unknown host name. This file contains the following informations:
- search keyword: defines the default domain name. For example if your computer is identified as "toto.my_domain.com" you are part of the domain "my_domain.com". If somebody, on the same network, wants to telnet (for example) your computer, he will use "telnet toto" instaed of "telnet toto.my_domain.com". The resolver will add ".my_domain.com" at the end.
- nameserver keyword: defines the names server(s) to consult if you ask for an unknown host name.
The /etc/services file contains informations on well-known network services (such as ftp, telnet, tftp, bootp, ...). For each service you specify:
Usually you don't have to edit this file. You may have to do it if you add a new service to your network (to uncoment a line).
/dev/ttySN is a special UNIX file. It represents the serial ports.
| Linux
| MS DOS |
| ttySN
| COM(N-1) |
| ttyS0
| COM1 |
| ttyS1
| COM2 |
| ...
| ...
|
| Notes
|
- for more informations the serial ports, see the serial-HOWTO.
- /dev/ttySN is a device file (There are 3 kinds of files: plain, directory and device file).
- to create /dev/ttySN you must use the mknode command. For example to create /dev/ttyS0, type:
"mknode /dev/ttyS0 c 4 64" for example.
"c" means characters devive.
"4" amd "64" represents the major and the minor number of this specific device.
- The major number is specific to a class of device (terminal, printer, disk, ...).
- The minor number represents a specific device within a class (ttyS0 is is the first serial device).
- Major and minor numbers are specifics to your installation of Linux. If you recompile your kernel (with new driver for example) you may have to recreate your device files because the (Major,Minor) may change.
|
|